- IEEE CS Standards
- Career Center
- Subscribe to Newsletter
- IEEE Standards
- For Industry Professionals
- For Students
- Launch a New Career
- Membership FAQ
- Membership FAQs
- Membership Grades
- Special Circumstances
- Discounts & Payments
- Distinguished Contributor Recognition
- Grant Programs
- Find a Local Chapter
- Find a Distinguished Visitor
- About Distinguished Visitors Program
- Find a Speaker on Early Career Topics
- Technical Communities
- Collabratec (Discussion Forum)
- My Subscriptions
- My Referrals
- Computer Magazine
- ComputingEdge Magazine
- Let us help make your event a success. EXPLORE PLANNING SERVICES
- Events Calendar
- Calls for Papers
- Conference Proceedings
- Conference Highlights
- Top 2024 Conferences
- Conference Sponsorship Options
- Conference Planning Services
- Conference Organizer Resources
- Virtual Conference Guide
- Get a Quote
- CPS Dashboard
- CPS Author FAQ
- CPS Organizer FAQ
- Find the latest in advanced computing research. VISIT THE DIGITAL LIBRARY
- Open Access
- Tech News Blog
- Author Guidelines
- Reviewer Information
- Guest Editor Information
- Editor Information
- Editor-in-Chief Information
- Volunteer Opportunities
- Video Library
- Member Benefits
- Institutional Library Subscriptions
- Advertising and Sponsorship
- Code of Ethics
- Educational Webinars
- Online Education
- Certifications
- Industry Webinars & Whitepapers
- Research Reports
- Bodies of Knowledge
- CS for Industry Professionals
- Resource Library
- Newsletters
- Women in Computing
- Digital Library Access
- Organize a Conference
- Run a Publication
- Become a Distinguished Speaker
- Participate in Standards Activities
- Peer Review Content
- Author Resources
- Publish Open Access
- Society Leadership
- Boards & Committees
- Local Chapters
- Governance Resources
- Conference Publishing Services
- Chapter Resources
- About the Board of Governors
- Board of Governors Members
- Diversity & Inclusion
- Open Volunteer Opportunities
- Award Recipients
- Student Scholarships & Awards
- Nominate an Election Candidate
- Nominate a Colleague
- Corporate Partnerships
- Conference Sponsorships & Exhibits
- Advertising
- Recruitment
- Publications
- Education & Career

Calls for Papers in Computer Science
About IEEE Annals of the History of Computing IEEE Annals of the History of Computing publishes work covering the broad history of computer technology, including technical, economic, political, social, cultural, institutional, and material aspects of computing. Featuring scholarly articles by historians, computer scientists, and interdisciplinary scholars in fields such as media studies and science and technology […]
About Computer (Magazine) Computer, the flagship publication of the IEEE Computer Society, publishes peer-reviewed articles written for and by computer researchers and practitioners representing the full spectrum of computing and information technology, from hardware to software and from emerging research to new applications. The aim is to provide more technical substance than trade magazines and […]
About IEEE Computer Graphics & Applications IEEE Computer Graphics and Applications (CG&A) bridges the theory and practice of computer graphics topics, including modeling, rendering, animation, (data) visualization, HCI/user interfaces, novel applications, hardware architectures, haptics, and virtual- and augmented-reality systems. From specific algorithms to full system implementations, CG&A offers a unique combination of peer-reviewed feature articles […]
Workshop & Panels proposal deadline: 1 November 2024 Tutorial proposal deadline: 1 December 2024 Panel proposal deadline: 6 January 2025 Research and industry paper submission deadline (2 pages max): 1 December 2024 15 January 2025 Acceptance notifications and reviewers’ comments: 1 March 2025 Final Camera-Ready copy deadline: 7 March 2025 Conference Date: 5-7 May 2025 IEEE Conference on Artificial Intelligence (IEEE […]
TP is now accepting submissions. To submit an article, please use the IEEE Author Portal. Detailed information on submitting your paper to an IEEE Computer Society publication can be found on the Author Guidelines page. TP provides a multidisciplinary forum for theoretical, methodological, engineering, and applications aspects of privacy and data protection. Privacy, in this […]
IEEE Pervasive Computing is launching a new “Research Brief” format to provide an accessible avenue for highlighting important results and perspectives based on new and published work. IEEE Pervasive Computing welcomes submissions that cover the role of computing in the physical world— as characterized by visions such as the Internet of Things and ubiquitous computing. […]
Important Dates Submissions due: 30 December 2024 Publication: July/August 2025 While the visualization community has made great strides over the last few decades, visualization research has traditionally centered on certain user groups, notably individuals without disabilities, overlooking the diverse capabilities and needs of a broader range of people. The disparities in sensory, cognitive, and motor […]
Publication: July/August 2025 A growing body of research in security and privacy focuses on threats and defenses that intersect with gender and sexuality (both sexual identity and sexual behavior or abuse). Existing research on threats includes a focus on digitally mediated intimate partner violence, image-based sexual abuse, and online hate & harassment. Existing research on […]
Call for Papers In recent years, artificial intelligence (AI) has become a powerful tool in the domain of networking systems, addressing complex tasks across edge computing, cloud computing, Internet-of-things, embedded systems, and NextG cellular wireless networks. Recent research has also unleashed the potential of AI techniques in optimizing various aspects of wireless and wired networking […]
Important Dates Title and Abstracts Due: 18 December 2024 (to [email protected]) Full Manuscripts Due: 15 January 2025 (via submission site) Publication date: Oct-Dec 2025 Fifteen years ago, IEEE Pervasive Computing published a groundbreaking special issue on “Cross-Reality Environments.” This concept, a fusion of ubiquitous sensor/actuator networks and immersive virtual worlds, envisioned a seamless electronic “nervous […]
Important Dates Submission deadline: 15 January 2025 Publication date: Jul/Aug 2025 Call for Papers Recent breakthroughs in Generative AI have sparked a new era of innovation. Generative AI models such as Large Language Models (LLMs) and Multimodal Large Language Models (MLLMs) are capable of creating high-quality content in diverse modalities including text, images, videos, and […]
Publication: September 2025 IEEE Transactions on Computers seeks original manuscripts for a special issue/section on Carbon Efficient Computer Architectures and Systems scheduled to appear in the September 2025 issue. Green and sustainable computing has long been relatively synonymous with energy-efficient computing. Over the last decade there is evidence that energy and resulting carbon and other […]
Paper due: 17 January 2025 Notification: 15 February 2025 Final Camera-Ready deadline: 28 February 2025 Conference Date: 23 – 25 June 2025 The Silicon Valley Cybersecurity Conference (SVCC) is an annual international conference in cybersecurity held at the heart of Silicon Valley, which is supported by the Silicon Valley Cybersecurity Institute (SVCSI). SVCC focuses on research […]
Important Dates Submissions due: 31 January 2025 Publication date: September 2025 Call for Papers Technology predictions have always been hard to make, yet they attract wide audiences because of their speculative nature and potential impact. Accurate predictions could have substantial impact on business. Degree of speculation as well as potential impact is dramatically amplified with radical […]
Important Dates Submission deadline: 1 February 2025 Publication date: Sep/Oct 2025 Call for Papers Background: As Artificial Intelligence (AI) advances, the need for transparency and interpretability in its decision-making processes becomes more pronounced, especially within the domain of affective computing. The capacity of AI systems to comprehend and react to human emotions introduces ethical considerations, […]
Important Dates Submission deadline: 1 February 2025 Publication date: July/August 2025 Call for Papers A vibrant AI ecosystem is developing across Middle East and Africa. There is little doubt that it has the potential to be transformative. In Africa over 2,400 businesses are reported to engage in AI (https://cioafrica.co/guide-to-unlocking-the-power-of-generative-ai/). Statista projects that the generative AI […]
Research and industry paper submission deadline (6 pages max): 10 February 2025 Acceptance notifications: 10 May 2025 Final Camera-Ready copy deadline: 30 May 2025 Special session proposal deadline: To be announced Conference Date: 6-9 July 2025 IEEE Symposium on Very Large Scale Integration (ISVLSI) The IEEE Symposium on VLSI (ISVLSI) is a globally recognized conference […]
Important Deadlines: Submission deadline: 13 February, 2025 Publication: September/October 2025 Deep Learning has made remarkable progress in various real-world applications ranging from robotics and image processing to medical applications. While there are many deep learning approaches and algorithms used today, few have made such a widespread impact as those belonging to the generative artificial intelligence […]
Publication: September/October 2025 The rapidly expanding data generated by advanced methods in biology is creating enormous challenges at the interface between humans and biological data that can be represented and analyzed visually. To meet these challenges, a blend of methodology from the visualization, bioinformatics and biology domains is required. This methodology encompasses perception and design […]
Important Deadlines: Abstract submission: February 23, 2025 Paper submission: March 2, 2025 Notification: April 18, 2025 Camera-ready and registration: May 25, 2025 Symposium dates: July 7-9, 2025 The IEEE International Symposium on On-Line Testing and Robust System Design (IOLTS) is an established forum for presenting novel ideas and experimental data on Online Testing techniques and, […]
Submissions due: February 27, 2025 Publication: Sept/Oct 2025 With the proliferation of mobile and edge computing devices, data generation continues to grow at an exponential rate, reaching an estimated 181 zettabytes processed per year by 2025. In response, computing systems large and small need to process ever-increasing amounts of data quickly and efficiently, leading to the […]
Important Dates Submission deadline: 1 March 2025 Publication date: Nov/Dec 2025 Call for Papers AI is influencing how we think about, carry out, and achieve a variety of tasks. From systems that recommend what to watch next to assistants that help write scientific articles to military applications that identify targets to hit, AI is challenging […]
Paper title/abstract due: March 7, 2025 Paper PDF due: March 21, 2025 Notification: May 13, 2025 Final Camera-Ready copy deadline: May 31, 2025 Conference Date: 21-26 September 2025 IEEE International Test Conference (ITS) The International Test Conference (ITC) is the world’s premier venue dedicated to the electronic test of devices, boards and systems—covering the complete cycle […]
Submissions due: March 13, 2025 Publication: Sept/Oct 2025 Topics of Interest Paper topics are not limited to hardware tapeouts. Papers that are software-centric papers relevant to the computer architecture audience are welcome in this track (e.g. datacenter software work, compiler work, accelerator software stack work), but they should adhere to the tenet that they must be […]
Important Dates Title and Abstracts Due: 17 March 2025 (email to [email protected]) Full Manuscripts Due: 31 March 2025 (via submission site) Publication date: Jul-Sep 2025 Call for Papers Marc Weiser famously envisioned “ubiquitous computing” as technology that fades into the background, seamlessly integrating ”into the fabric of everyday life until they are indistinguishable from it”. […]
By seamlessly integrating the physical and the virtual worlds, metaverse offers a platform of a new social ecosystem, dealing with digital twins and empowering virtual-reality symbiosis, which has been widely regarded as one of the key enablers of our future society with profound social and economic impacts. Empowered by the new generation of digital technologies […]
Important Dates Submissions due: 31 March 2025 Publication date: December 2025 Call for Papers Smart ecosystems are emerging worldwide, addressing the need for both resilient and sustainable development, meeting key performance indicators that consider social and economic factors as well as technological ones. The growth of such smart ecosystems is no longer constrained to urban scenarios […]
DEADLINES: Open for Submissions: 1 January 2025 Submissions due: 31 March 2025 Publication: Oct-Dec 2025 TOPIC SUMMARY: Nowadays, all over the world, the number of ICT investments in health and well-being is rapidly increasing. In this context, there is a growing interest in telemedicine that allows the provisioning of various kinds of health-related services […]
Publication: March/April 2026 The energy footprint of software, software engineering, and software-intensive systems poses a significant concern. Energy-hungry software-intensive systems, such as blockchain applications and cryptocurrencies, the pervasive integration and usage of central cloud and edge services and applications, along with AI-enabled systems, contribute to this issue. In addition, the global digital transformation of all […]
Important Dates Submissions Due: 9 April 2025 *Expected* Publication Issue: Jan/Feb 2026 Call for Papers Motivation and Scope “Software for all and by all” is the future of humanity. AIware, i.e., AI-powered software, has the potential to democratize software creation. The definition of software along with many Software Engineering (SE) aspects, processes, tools, platforms, and […]
Important Dates Workshop, proposal papers due – 15 October 2024 1 November 2024 Workshop, proposal notification – 15 November 2024 Full symposium paper notification – 7 April 2025 Workshop papers due – 15 April 2025 Workshop papers notification – 1 May 2025 Camera-ready copy – 1 June 2025 Call for Papers COMPSAC 2025: Harnessing the […]
Important Deadlines: Submission deadline: 24 April 2025 Publication: November/December 2025 Artificial intelligence (AI) has made significant strides across various fields. However, its end-to-end automation often overlooks the nuances of human needs and expectations, particularly in creative domains like graphics and visualization design. These fields demand human expertise, creativity, and iterative development – qualities that AI […]
Submissions due: April 25, 2025 Publication: Nov/Dec 2025 For years, the computational landscape, stretching from data centers and supercomputers to simple home devices, has predominantly depended on general-purpose processors which were sustainable while Moore’s law guaranteed that chip transistor counts would double approximately every two years. Today, however, as the pace of Moore’s law decelerates, we […]
Important Dates Title and Abstracts Due: 1 December 2024 (to [email protected], [email protected]) Full Manuscripts Due: 11 November 2025 (via submission site) Publication: Apr-Jun 2026 Call for Papers What were the material, technical, epistemic, cultural, and political conditions that made the built environment computable? And, conversely, what are the implications of emplacing the history of computing […]
IEEE Transactions on Computers (TC), the flagship journal for the IEEE Computer Society, is a monthly publication with a wide distribution to researchers, developers, technical managers, and educators in the computer field. It publishes papers on research in areas of current interest to the readers, including but not limited to the following: Computer organizations and […]
CiSE accepts submissions on an ongoing basis for the following three tracks: Data* Reproducible Research Software Engineering Please see the individual calls for papers below for details. Data* Track – Call for Papers Submission and publication: Ongoing Track editors: Ilkay Altintas (San Diego Supercomputer Center) and Nicola Ferrier (Argonne National Laboratory) The data-centric era is […]
IEEE Transactions on Affective Computing is a cross-disciplinary and international archive journal aimed at disseminating results of research on the design of systems that can recognize, interpret, and simulate human emotions and related affective phenomena. The journal publishes original research on the principles and theories explaining why and how affective factors condition interaction between humans […]
IEEE Transactions on Emerging Topics in Computing (TETC) seeks original manuscripts for submission under Technical Tracks. In a track, the technical contents of a submitted manuscript must be both of research type and of an emerging nature, and must fall within the scope and competencies of the Computer Society. Purely theoretical, technological, or lacking methodological-and-generality papers are […]

Become a Member and Save on Publications
- Learn what’s new and what’s next with access to Computer magazine.
- Access a wealth of computing information – at your fingertips with the Computer Society Digital Library.
Grady Booch Chief Scientist for Software Engineering / IBM Research
open access papers
Showing 1 - 12 of 41 resources. too many results use the search filters to refine your search..
- Sort by: Relevance
- Title (A-Z)
- Title (Z-A)

- SSCS Members: Free IEEE Members: Free Non-members: Free

Share this page:
Top 10 Published Articles of IEEE Access

Over the past ten years, IEEE Access has published some of the most groundbreaking research in electrical and electronics engineering and computer science. In celebration of the 10 Year Publishing Anniversary , our Editors have selected the Top 10 articles published in IEEE Access over the last decade based on downloads, citations, and overall impact in IEEE fields of interest.
Millimeter wave mobile communications for 5g cellular: it will work (published in 2013).
Authors : Theodore S. Rappaport, Shu Sun, Rimma Mayzus, Hang Zhao, Yaniv Azar, Kevin Wang, George N. Wong, Jocelyn K. Schulz, Mathew Samimi, Felix Gutierrez
Abstract : The global bandwidth shortage facing wireless carriers has motivated the exploration of the underutilized millimeter wave (mm-wave) frequency spectrum for future broadband cellular communication networks. There is, however, little knowledge about cellular mm-wave propagation in densely populated indoor and outdoor environments. Obtaining this information is vital for the design and operation of future fifth generation cellular networks that use the mm-wave spectrum. In this paper, we present the motivation for new mm-wave cellular systems, methodology, and hardware for measurements and offer a variety of measurement results that show 28 and 38 GHz frequencies can be used when employing steerable directional antennas at base stations and mobile devices.
3D Printing for the Rapid Prototyping of Structural Electronics (Published in 2014)
Authors : Eric Macdonald, Rudy Salas, David Espalin, Mireya Perez, Efrain Aguilera, Dan Muse, Ryan B. Wicker
Abstract : In new product development, time to market (TTM) is critical for the success and profitability of next generation products. When these products include sophisticated electronics encased in 3D packaging with complex geometries and intricate detail, TTM can be compromised – resulting in lost opportunity. The use of advanced 3D printing technology enhanced with component placement and electrical interconnect deposition can provide electronic prototypes that now can be rapidly fabricated in comparable time frames as traditional 2D bread-boarded prototypes; however, these 3D prototypes include the advantage of being embedded within more appropriate shapes in order to authentically prototype products earlier in the development cycle. The fabrication freedom offered by 3D printing techniques, such as stereolithography and fused deposition modeling have recently been explored in the context of 3D electronics integration – referred to as 3D structural electronics or 3D printed electronics. Enhanced 3D printing may eventually be employed to manufacture end-use parts and thus offer unit-level customization with local manufacturing; however, until the materials and dimensional accuracies improve (an eventuality), 3D printing technologies can be employed to reduce development times by providing advanced geometrically appropriate electronic prototypes. This paper describes the development process used to design a novelty six-sided gaming die. The die includes a microprocessor and accelerometer, which together detect motion and upon halting, identify the top surface through gravity and illuminate light-emitting diodes for a striking effect. By applying 3D printing of structural electronics to expedite prototyping, the development cycle was reduced from weeks to hours.
C2PS: A Digital Twin Architecture Reference Model for the Cloud-Based Cyber-Physical Systems (Published in 2017)
Authors : Kazi Masudul Alam, Abdulmotaleb El Saddik
Abstract : Cyber-physical system (CPS) is a new trend in the Internet-of-Things related research works, where physical systems act as the sensors to collect real-world information and communicate them to the computation modules (i.e. cyber layer), which further analyze and notify the findings to the corresponding physical systems through a feedback loop. Contemporary researchers recommend integrating cloud technologies in the CPS cyber layer to ensure the scalability of storage, computation, and cross domain communication capabilities. Though there exist a few descriptive models of the cloud-based CPS architecture, it is important to analytically describe the key CPS properties: computation, control, and communication. In this paper, we present a digital twin architecture reference model for the cloud-based CPS, C2PS, where we analytically describe the key properties of the C2PS. The model helps in identifying various degrees of basic and hybrid computation-interaction modes in this paradigm. We have designed C2PS smart interaction controller using a Bayesian belief network, so that the system dynamically considers current contexts. The composition of fuzzy rule base with the Bayes network further enables the system with reconfiguration capability. We also describe analytically, how C2PS subsystem communications can generate even more complex system-of-systems. Later, we present a telematics-based prototype driving assistance application for the vehicular domain of C2PS, VCPS, to demonstrate the efficacy of the architecture reference model.
Peeking Inside the Black-Box: A Survey on Explainable Artificial Intelligence (XAI) (Published in 2018)
Authors : Amina Adadi, Mohammed Berrada
Abstract : At the dawn of the fourth industrial revolution, we are witnessing a fast and widespread adoption of artificial intelligence (AI) in our daily life, which contributes to accelerating the shift towards a more algorithmic society. However, even with such unprecedented advancements, a key impediment to the use of AI-based systems is that they often lack transparency. Indeed, the black-box nature of these systems allows powerful predictions, but it cannot be directly explained. This issue has triggered a new debate on explainable AI (XAI). A research field holds substantial promise for improving trust and transparency of AI-based systems. It is recognized as the sine qua non for AI to continue making steady progress without disruption. This survey provides an entry point for interested researchers and practitioners to learn key aspects of the young and rapidly growing body of research related to XAI. Through the lens of the literature, we review the existing approaches regarding the topic, discuss trends surrounding its sphere, and present major research trajectories.
5G Evolution: A View on 5G Cellular Technology Beyond 3GPP Release 15 (Published in 2019)
Authors : Amitabha Ghosh, Andreas Maeder, Matthew Baker, Devaki Chandramouli
Abstract : The 5G System is being developed and enhanced to provide unparalleled connectivity to connect everyone and everything, everywhere. The first version of the 5G System, based on the Release 15 (“Rel-15”) version of the specifications developed by 3GPP, comprising the 5G Core (5GC) and 5G New Radio (NR) with 5G User Equipment (UE), is currently being deployed commercially throughout the world both at sub-6 GHz and at mmWave frequencies. Concurrently, the second phase of 5G is being standardized by 3GPP in the Release 16 (“Rel-16”) version of the specifications which will be completed by March 2020. While the main focus of Rel-15 was on enhanced mobile broadband services, the focus of Rel-16 is on new features for URLLC (Ultra-Reliable Low Latency Communication) and Industrial IoT, including Time Sensitive Communication (TSC), enhanced Location Services, and support for Non-Public Networks (NPNs). In addition, some crucial new features, such as NR on unlicensed bands (NR-U), Integrated Access & Backhaul (IAB) and NR Vehicle-to-X (V2X), are also being introduced as part of Rel-16, as well as enhancements for massive MIMO, wireless and wireline convergence, the Service Based Architecture (SBA) and Network Slicing. Finally, the number of use cases, types of connectivity and users, and applications running on top of 5G networks, are all expected to increase dramatically, thus motivating additional security features to counter security threats which are expected to increase in number, scale and variety. In this paper, we discuss the Rel-16 features and provide an outlook towards Rel-17 and beyond, covering both new features and enhancements of existing features. 5G Evolution will focus on three main areas: enhancements to features introduced in Rel-15 and Rel-16, features that are needed for operational enhancements, and new features to further expand the applicability of the 5G System to new markets and use cases.
Wireless Communications Through Reconfigurable Intelligent Surfaces (Published in 2019)
Authors : Ertugrul Basar, Marco Di Renzo, Julien De Rosny, Merouane Debbah, Mohamed-Slim Alouini, Rui Zhang
Abstract : The future of mobile communications looks exciting with the potential new use cases and challenging requirements of future 6th generation (6G) and beyond wireless networks. Since the beginning of the modern era of wireless communications, the propagation medium has been perceived as a randomly behaving entity between the transmitter and the receiver, which degrades the quality of the received signal due to the uncontrollable interactions of the transmitted radio waves with the surrounding objects. The recent advent of reconfigurable intelligent surfaces in wireless communications enables, on the other hand, network operators to control the scattering, reflection, and refraction characteristics of the radio waves, by overcoming the negative effects of natural wireless propagation. Recent results have revealed that reconfigurable intelligent surfaces can effectively control the wavefront, e.g., the phase, amplitude, frequency, and even polarization, of the impinging signals without the need of complex decoding, encoding, and radio frequency processing operations. Motivated by the potential of this emerging technology, the present article is aimed to provide the readers with a detailed overview and historical perspective on state-of-the-art solutions, and to elaborate on the fundamental differences with other technologies, the most important open research issues to tackle, and the reasons why the use of reconfigurable intelligent surfaces necessitates to rethink the communication-theoretic models currently employed in wireless networks. This article also explores theoretical performance limits of reconfigurable intelligent surface-assisted communication systems using mathematical techniques and elaborates on the potential use cases of intelligent surfaces in 6G and beyond wireless networks.
Beyond Herd Immunity Against Strategic Attackers (Published in 2020)
Authors : Vilc Queupe, Leandro Pfleger De Aguiar, Daniel Sadoc Menasche, Cabral Lima, Italo Cunha, Eitan Altman, Rachid El-Azouzi, Francesco De Pellegrini, Alberto Avritzer, Michael Grottke
Abstract : Herd immunity, one of the most fundamental concepts in network epidemics, occurs when a large fraction of the population of devices is immune against a virus or malware. The few individuals who have not taken countermeasures against the threat are assumed to have very low chances of infection, as they are indirectly protected by the rest of the devices in the network. Although very fundamental, herd immunity does not account for strategic attackers scanning the network for vulnerable nodes. In face of such attackers, nodes who linger vulnerable in the network become easy targets, compromising cybersecurity. In this paper, we propose an analytical model which allows us to capture the impact of countermeasures against attackers when both endogenous as well as exogenous infections coexist. Using the proposed model, we show that a diverse set of potential attacks produces non-trivial equilibria, some of which go counter to herd immunity; e.g., our model suggests that nodes should adopt countermeasures even when the remainder of the nodes has already decided to do so.

Unsupervised K-Means Clustering Algorithm (Published in 2020)
Authors : Kristina P. Sinaga, Miin-Shen Yang
Abstract : The k-means algorithm is generally the most known and used clustering method. There are various extensions of k-means to be proposed in the literature. Although it is an unsupervised learning to clustering in pattern recognition and machine learning, the k-means algorithm and its extensions are always influenced by initializations with a necessary number of clusters a priori. That is, the k-means algorithm is not exactly an unsupervised clustering method. In this paper, we construct an unsupervised learning schema for the k-means algorithm so that it is free of initializations without parameter selection and can also simultaneously find an optimal number of clusters. That is, we propose a novel unsupervised k-means (U-k-means) clustering algorithm with automatically finding an optimal number of clusters without giving any initialization and parameter selection. The computational complexity of the proposed U-k-means clustering algorithm is also analyzed. Comparisons between the proposed U-k-means and other existing methods are made. Experimental results and comparisons actually demonstrate these good aspects of the proposed U-k-means clustering algorithm.
Enabling Large Intelligent Surfaces With Compressive Sensing and Deep Learning (Published in 2021)
Authors : Abdelrahman Taha, Muhammad Alrabeiah, Ahmed Alkhateeb
Abstract : Employing large intelligent surfaces (LISs) is a promising solution for improving the coverage and rate of future wireless systems. These surfaces comprise massive numbers of nearly-passive elements that interact with the incident signals, for example by reflecting them, in a smart way that improves the wireless system performance. Prior work focused on the design of the LIS reflection matrices assuming full channel knowledge. Estimating these channels at the LIS, however, is a key challenging problem. With the massive number of LIS elements, channel estimation or reflection beam training will be associated with (i) huge training overhead if all the LIS elements are passive (not connected to a baseband) or with (ii) prohibitive hardware complexity and power consumption if all the elements are connected to the baseband through a fully-digital or hybrid analog/digital architecture. This paper proposes efficient solutions for these problems by leveraging tools from compressive sensing and deep learning. First, a novel LIS architecture based on sparse channel sensors is proposed. In this architecture, all the LIS elements are passive except for a few elements that are active (connected to the baseband). We then develop two solutions that design the LIS reflection matrices with negligible training overhead. In the first approach, we leverage compressive sensing tools to construct the channels at all the LIS elements from the channels seen only at the active elements. In the second approach, we develop a deep-learning based solution where the LIS learns how to interact with the incident signal given the channels at the active elements, which represent the state of the environment and transmitter/receiver locations. We show that the achievable rates of the proposed solutions approach the upper bound, which assumes perfect channel knowledge, with negligible training overhead and with only a few active elements, making them promising for future LIS systems.
DNN-Based Indoor Localization Under Limited Dataset Using GANs and Semi-Supervised Learning (Published in 2022)
Authors : Wafa Njima, Ahmad Bazzi, Marwa Chafii
Abstract : Indoor localization techniques based on supervised learning deliver great performance accuracy while maintaining low online complexity. However, such systems require massive amounts of data for offline training, which necessitates costly measurements. The essence of this paper is twofold with the purpose of providing solutions to missing data of different nature: available unlabeled data and missing unlabeled data. In both cases, we rely on a few labeled available data, which is costly yet insufficient to achieve a high localization accuracy. To address the problem of available unlabeled data, a weighted semi-supervised DNN-based indoor localization approach leveraging pseudo-labeling methods in combination with real labeled samples and inexpensive pseudo-labeled samples is proposed in order to boost localization accuracy, while overcoming the high cost of collecting additional labeled data. As for the extreme case of unavailable unlabeled data, we propose an alternative localization system generating fake fingerprints based on generative adversarial networks (GANs) named ’Weighted GAN based indoor localization’. Furthermore, a deep neural network is trained on a mixed dataset containing both real collected and fake produced data samples using a similar weighting technique in order to improve location prediction performance and avoids overfitting. In terms of localization accuracy, our proposed localization approaches outperform conventional supervised localization schemes utilizing the same collection of real labeled samples. We have tested our proposed methods on both simulated data and experimental data from the publicly available UJIIndoorLoc database, which is built to test indoor positioning systems relying on Wi-Fi fingerprints. Results based on experimental data provide the localization accuracy increase compared to the classical supervised learning method using the same set of labeled collected data when using the weighted semi-supervised and the weighted-GAN approaches by $10.11~\%$ and $8.53~\%$ , respectively.
At a Glance
- Journal: IEEE Access
- Format: Open Access
- Frequency: Continuous
- Submission to Publication: 4-6 weeks (typical)
- Topics: All topics in IEEE
- Average Acceptance Rate: 27%
- Impact Factor: 3.4
- Model: Binary Peer Review
- Article Processing Charge: US $1,995
Featured Articles
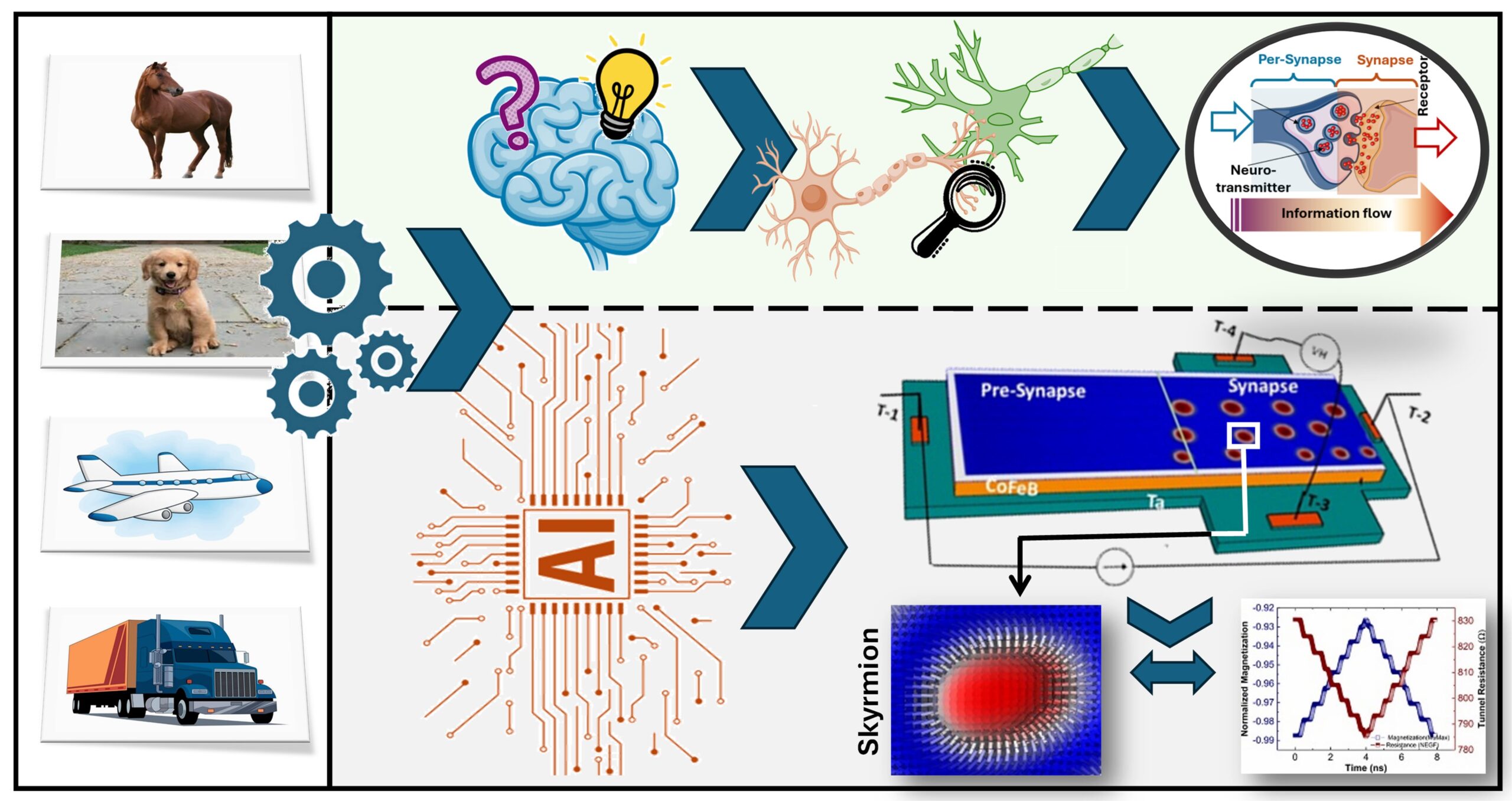
Controlling the Skyrmion Density and Size for Quantized Convolutional Neural Network
View in IEEE Xplore
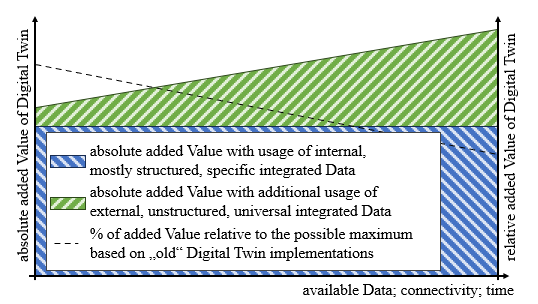
Data Integration for Digital Twins in Industrial Automation: A Systematic Literature Review
A Lightweight Authentication Scheme for Power IoT Based on PUF and Chebyshev Chaotic Map
Submission guidelines.
© 2024 IEEE - All rights reserved. Use of this website signifies your agreement to the IEEE TERMS AND CONDITIONS.
A not-for-profit organization, IEEE is the world’s largest technical professional organization dedicated to advancing technology for the benefit of humanity.
AWARD RULES:
NO PURCHASE NECESSARY TO ENTER OR WIN. A PURCHASE WILL NOT INCREASE YOUR CHANCES OF WINNING.
These rules apply to the “2024 IEEE Access Best Video Award Part 2″ (the “Award”).
- Sponsor: The Sponsor of the Award is The Institute of Electrical and Electronics Engineers, Incorporated (“IEEE”) on behalf of IEEE Access , 445 Hoes Lane, Piscataway, NJ 08854-4141 USA (“Sponsor”).
- Eligibility: Award is open to residents of the United States of America and other countries, where permitted by local law, who are the age of eighteen (18) and older. Employees of Sponsor, its agents, affiliates and their immediate families are not eligible to enter Award. The Award is subject to all applicable state, local, federal and national laws and regulations. Entrants may be subject to rules imposed by their institution or employer relative to their participation in Awards and should check with their institution or employer for any relevant policies. Void in locations and countries where prohibited by law.
- Agreement to Official Rules : By participating in this Award, entrants agree to abide by the terms and conditions thereof as established by Sponsor. Sponsor reserves the right to alter any of these Official Rules at any time and for any reason. All decisions made by Sponsor concerning the Award including, but not limited to the cancellation of the Award, shall be final and at its sole discretion.
- How to Enter: This Award opens on July 1, 2024 at 12:00 AM ET and all entries must be received by 11:59 PM ET on December 31, 2024 (“Promotional Period”).
Entrant must submit a video with an article submission to IEEE Access . The video submission must clearly be relevant to the submitted manuscript. Only videos that accompany an article that is accepted for publication in IEEE Access will qualify. The video may be simulations, demonstrations, or interviews with other experts, for example. Your video file should not exceed 100 MB.
Entrants can enter the Award during Promotional Period through the following method:
- The IEEE Author Portal : Entrants can upload their video entries while submitting their article through the IEEE Author Portal submission site .
- Review and Complete the Terms and Conditions: After submitting your manuscript and video through the IEEE Author Portal, entrants should then review and sign the Terms and Conditions .
Entrants who have already submitted a manuscript to IEEE Access without a video can still submit a video for inclusion in this Award so long as the video is submitted within 7 days of the article submission date. The video can be submitted via email to the article administrator. All videos must undergo peer review and be accepted along with the article submission. Videos may not be submitted after an article has already been accepted for publication.
The criteria for an article to be accepted for publication in IEEE Access are:
- The article must be original writing that enhances the existing body of knowledge in the given subject area. Original review articles and surveys are acceptable even if new data/concepts are not presented.
- Results reported must not have been submitted or published elsewhere (although expanded versions of conference publications are eligible for submission).
- Experiments, statistics, and other analyses must be performed to a high technical standard and are described in sufficient detail.
- Conclusions must be presented in an appropriate fashion and are supported by the data.
- The article must be written in standard English with correct grammar.
- Appropriate references to related prior published works must be included.
- The article must fall within the scope of IEEE Access
- Must be in compliance with the IEEE PSPB Operations Manual.
- Completion of the required IEEE intellectual property documents for publication.
- At the discretion of the IEEE Access Editor-in-Chief.
- Disqualification: The following items will disqualify a video from being considered a valid submission:
- The video is not original work.
- A video that is not accompanied with an article submission.
- The article and/or video is rejected during the peer review process.
- The article and/or video topic does not fit into the scope of IEEE Access .
- The article and/or do not follow the criteria for publication in IEEE Access .
- Videos posted in a comment on IEEE Xplore .
- Content is off-topic, offensive, obscene, indecent, abusive or threatening to others.
- Infringes the copyright, trademark or other right of any third party.
- Uploads viruses or other contaminating or destructive features.
- Is in violation of any applicable laws or regulations.
- Is not in English.
- Is not provided within the designated submission time.
- Entrant does not agree and sign the Terms and Conditions document.
Entries must be original. Entries that copy other entries, or the intellectual property of anyone other than the Entrant, may be removed by Sponsor and the Entrant may be disqualified. Sponsor reserves the right to remove any entry and disqualify any Entrant if the entry is deemed, in Sponsor’s sole discretion, to be inappropriate.
- Entrant’s Warranty and Authorization to Sponsor: By entering the Award, entrants warrant and represent that the Award Entry has been created and submitted by the Entrant. Entrant certifies that they have the ability to use any image, text, video, or other intellectual property they may upload and that Entrant has obtained all necessary permissions. IEEE shall not indemnify Entrant for any infringement, violation of publicity rights, or other civil or criminal violations. Entrant agrees to hold IEEE harmless for all actions related to the submission of an Entry. Entrants further represent and warrant, if they reside outside of the United States of America, that their participation in this Award and acceptance of a prize will not violate their local laws.
- Intellectual Property Rights: Entrant grants Sponsor an irrevocable, worldwide, royalty free license to use, reproduce, distribute, and display the Entry for any lawful purpose in all media whether now known or hereinafter created. This may include, but is not limited to, the IEEE A ccess website, the IEEE Access YouTube channel, the IEEE Access IEEE TV channel, IEEE Access social media sites (LinkedIn, Facebook, Twitter, IEEE Access Collabratec Community), and the IEEE Access Xplore page. Facebook/Twitter/Microsite usernames will not be used in any promotional and advertising materials without the Entrants’ expressed approval.
- Number of Prizes Available, Prizes, Approximate Retail Value and Odds of winning Prizes: Two (2) promotional prizes of $350 USD Amazon gift cards. One (1) grand prize of a $500 USD Amazon gift card. Prizes will be distributed to the winners after the selection of winners is announced. Odds of winning a prize depend on the number of eligible entries received during the Promotional Period. Only the corresponding author of the submitted manuscript will receive the prize.
The grand prize winner may, at Sponsor’ discretion, have his/her article and video highlighted in media such as the IEEE Access Xplore page and the IEEE Access social media sites.
The prize(s) for the Award are being sponsored by IEEE. No cash in lieu of prize or substitution of prize permitted, except that Sponsor reserves the right to substitute a prize or prize component of equal or greater value in its sole discretion for any reason at time of award. Sponsor shall not be responsible for service obligations or warranty (if any) in relation to the prize(s). Prize may not be transferred prior to award. All other expenses associated with use of the prize, including, but not limited to local, state, or federal taxes on the Prize, are the sole responsibility of the winner. Winner(s) understand that delivery of a prize may be void where prohibited by law and agrees that Sponsor shall have no obligation to substitute an alternate prize when so prohibited. Amazon is not a sponsor or affiliated with this Award.
- Selection of Winners: Promotional prize winners will be selected based on entries received during the Promotional Period. The sponsor will utilize an Editorial Panel to vote on the best video submissions. Editorial Panel members are not eligible to participate in the Award. Entries will be ranked based on three (3) criteria:
- Presentation of Technical Content
- Quality of Video
Upon selecting a winner, the Sponsor will notify the winner via email. All potential winners will be notified via their email provided to the sponsor. Potential winners will have five (5) business days to respond after receiving initial prize notification or the prize may be forfeited and awarded to an alternate winner. Potential winners may be required to sign an affidavit of eligibility, a liability release, and a publicity release. If requested, these documents must be completed, signed, and returned within ten (10) business days from the date of issuance or the prize will be forfeited and may be awarded to an alternate winner. If prize or prize notification is returned as undeliverable or in the event of noncompliance with these Official Rules, prize will be forfeited and may be awarded to an alternate winner.
- General Prize Restrictions: No prize substitutions or transfer of prize permitted, except by the Sponsor. Import/Export taxes, VAT and country taxes on prizes are the sole responsibility of winners. Acceptance of a prize constitutes permission for the Sponsor and its designees to use winner’s name and likeness for advertising, promotional and other purposes in any and all media now and hereafter known without additional compensation unless prohibited by law. Winner acknowledges that neither Sponsor, Award Entities nor their directors, employees, or agents, have made nor are in any manner responsible or liable for any warranty, representation, or guarantee, express or implied, in fact or in law, relative to any prize, including but not limited to its quality, mechanical condition or fitness for a particular purpose. Any and all warranties and/or guarantees on a prize (if any) are subject to the respective manufacturers’ terms therefor, and winners agree to look solely to such manufacturers for any such warranty and/or guarantee.
11.Release, Publicity, and Privacy : By receipt of the Prize and/or, if requested, by signing an affidavit of eligibility and liability/publicity release, the Prize Winner consents to the use of his or her name, likeness, business name and address by Sponsor for advertising and promotional purposes, including but not limited to on Sponsor’s social media pages, without any additional compensation, except where prohibited. No entries will be returned. All entries become the property of Sponsor. The Prize Winner agrees to release and hold harmless Sponsor and its officers, directors, employees, affiliated companies, agents, successors and assigns from and against any claim or cause of action arising out of participation in the Award.
Sponsor assumes no responsibility for computer system, hardware, software or program malfunctions or other errors, failures, delayed computer transactions or network connections that are human or technical in nature, or for damaged, lost, late, illegible or misdirected entries; technical, hardware, software, electronic or telephone failures of any kind; lost or unavailable network connections; fraudulent, incomplete, garbled or delayed computer transmissions whether caused by Sponsor, the users, or by any of the equipment or programming associated with or utilized in this Award; or by any technical or human error that may occur in the processing of submissions or downloading, that may limit, delay or prevent an entrant’s ability to participate in the Award.
Sponsor reserves the right, in its sole discretion, to cancel or suspend this Award and award a prize from entries received up to the time of termination or suspension should virus, bugs or other causes beyond Sponsor’s control, unauthorized human intervention, malfunction, computer problems, phone line or network hardware or software malfunction, which, in the sole opinion of Sponsor, corrupt, compromise or materially affect the administration, fairness, security or proper play of the Award or proper submission of entries. Sponsor is not liable for any loss, injury or damage caused, whether directly or indirectly, in whole or in part, from downloading data or otherwise participating in this Award.
Representations and Warranties Regarding Entries: By submitting an Entry, you represent and warrant that your Entry does not and shall not comprise, contain, or describe, as determined in Sponsor’s sole discretion: (A) false statements or any misrepresentations of your affiliation with a person or entity; (B) personally identifying information about you or any other person; (C) statements or other content that is false, deceptive, misleading, scandalous, indecent, obscene, unlawful, defamatory, libelous, fraudulent, tortious, threatening, harassing, hateful, degrading, intimidating, or racially or ethnically offensive; (D) conduct that could be considered a criminal offense, could give rise to criminal or civil liability, or could violate any law; (E) any advertising, promotion or other solicitation, or any third party brand name or trademark; or (F) any virus, worm, Trojan horse, or other harmful code or component. By submitting an Entry, you represent and warrant that you own the full rights to the Entry and have obtained any and all necessary consents, permissions, approvals and licenses to submit the Entry and comply with all of these Official Rules, and that the submitted Entry is your sole original work, has not been previously published, released or distributed, and does not infringe any third-party rights or violate any laws or regulations.
12.Disputes: EACH ENTRANT AGREES THAT: (1) ANY AND ALL DISPUTES, CLAIMS, AND CAUSES OF ACTION ARISING OUT OF OR IN CONNECTION WITH THIS AWARD, OR ANY PRIZES AWARDED, SHALL BE RESOLVED INDIVIDUALLY, WITHOUT RESORTING TO ANY FORM OF CLASS ACTION, PURSUANT TO ARBITRATION CONDUCTED UNDER THE COMMERCIAL ARBITRATION RULES OF THE AMERICAN ARBITRATION ASSOCIATION THEN IN EFFECT, (2) ANY AND ALL CLAIMS, JUDGMENTS AND AWARDS SHALL BE LIMITED TO ACTUAL OUT-OF-POCKET COSTS INCURRED, INCLUDING COSTS ASSOCIATED WITH ENTERING THIS AWARD, BUT IN NO EVENT ATTORNEYS’ FEES; AND (3) UNDER NO CIRCUMSTANCES WILL ANY ENTRANT BE PERMITTED TO OBTAIN AWARDS FOR, AND ENTRANT HEREBY WAIVES ALL RIGHTS TO CLAIM, PUNITIVE, INCIDENTAL, AND CONSEQUENTIAL DAMAGES, AND ANY OTHER DAMAGES, OTHER THAN FOR ACTUAL OUT-OF-POCKET EXPENSES, AND ANY AND ALL RIGHTS TO HAVE DAMAGES MULTIPLIED OR OTHERWISE INCREASED. ALL ISSUES AND QUESTIONS CONCERNING THE CONSTRUCTION, VALIDITY, INTERPRETATION AND ENFORCEABILITY OF THESE OFFICIAL RULES, OR THE RIGHTS AND OBLIGATIONS OF ENTRANT AND SPONSOR IN CONNECTION WITH THE AWARD, SHALL BE GOVERNED BY, AND CONSTRUED IN ACCORDANCE WITH, THE LAWS OF THE STATE OF NEW JERSEY, WITHOUT GIVING EFFECT TO ANY CHOICE OF LAW OR CONFLICT OF LAW, RULES OR PROVISIONS (WHETHER OF THE STATE OF NEW JERSEY OR ANY OTHER JURISDICTION) THAT WOULD CAUSE THE APPLICATION OF THE LAWS OF ANY JURISDICTION OTHER THAN THE STATE OF NEW JERSEY. SPONSOR IS NOT RESPONSIBLE FOR ANY TYPOGRAPHICAL OR OTHER ERROR IN THE PRINTING OF THE OFFER OR ADMINISTRATION OF THE AWARD OR IN THE ANNOUNCEMENT OF THE PRIZES.
- Limitation of Liability: The Sponsor, Award Entities and their respective parents, affiliates, divisions, licensees, subsidiaries, and advertising and promotion agencies, and each of the foregoing entities’ respective employees, officers, directors, shareholders and agents (the “Released Parties”) are not responsible for incorrect or inaccurate transfer of entry information, human error, technical malfunction, lost/delayed data transmissions, omission, interruption, deletion, defect, line failures of any telephone network, computer equipment, software or any combination thereof, inability to access web sites, damage to a user’s computer system (hardware and/or software) due to participation in this Award or any other problem or error that may occur. By entering, participants agree to release and hold harmless the Released Parties from and against any and all claims, actions and/or liability for injuries, loss or damage of any kind arising from or in connection with participation in and/or liability for injuries, loss or damage of any kind, to person or property, arising from or in connection with participation in and/or entry into this Award, participation is any Award-related activity or use of any prize won. Entry materials that have been tampered with or altered are void. If for any reason this Award is not capable of running as planned, or if this Award or any website associated therewith (or any portion thereof) becomes corrupted or does not allow the proper playing of this Award and processing of entries per these rules, or if infection by computer virus, bugs, tampering, unauthorized intervention, affect the administration, security, fairness, integrity, or proper conduct of this Award, Sponsor reserves the right, at its sole discretion, to disqualify any individual implicated in such action, and/or to cancel, terminate, modify or suspend this Award or any portion thereof, or to amend these rules without notice. In the event of a dispute as to who submitted an online entry, the entry will be deemed submitted by the authorized account holder the email address submitted at the time of entry. “Authorized Account Holder” is defined as the person assigned to an email address by an Internet access provider, online service provider or other organization responsible for assigning email addresses for the domain associated with the email address in question. Any attempt by an entrant or any other individual to deliberately damage any web site or undermine the legitimate operation of the Award is a violation of criminal and civil laws and should such an attempt be made, the Sponsor reserves the right to seek damages and other remedies from any such person to the fullest extent permitted by law. This Award is governed by the laws of the State of New Jersey and all entrants hereby submit to the exclusive jurisdiction of federal or state courts located in the State of New Jersey for the resolution of all claims and disputes. Facebook, LinkedIn, Twitter, G+, YouTube, IEEE Xplore , and IEEE TV are not sponsors nor affiliated with this Award.
- Award Results and Official Rules: To obtain the identity of the prize winner and/or a copy of these Official Rules, send a self-addressed stamped envelope to Kimberly Rybczynski, IEEE, 445 Hoes Lane, Piscataway, NJ 08854-4141 USA.
Role, Methodology, and Measurement of Cognitive Load in Computer Science and Information Systems Research
Ieee account.
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.

IMAGES
COMMENTS
Unlock peer-reviewed research and expert commentary from the world's trusted resource for computer science and engineering information. IEEE.org; IEEE CS Standards; ... including Plan S. OJ-CS and TP content are available for free in the IEEE Computer Society ... Read our author guidelines for instructions on writing and submitting your paper.
IEEE Xplore, delivering full text access to the world's highest quality technical literature in engineering and technology. | IEEE Xplore ... Selected Papers On Computer Science Published in: IEEE Annals of the History of Computing ( Volume: 20 , Issue: 1 , Jan.-March 1998) Article #: Page(s): 82 - 83. Date of Publication: 31 March 1998 . ISSN ...
Read all the papers in 2024 International Conference on Artificial Intelligence, Computer, Data Sciences and Applications (ACDSA) | IEEE Conference | IEEE Xplor
Generative artificial intelligence can make powerful artifacts when used at scale, but developing trust in these artifacts and controlling their creation are es
In addition, IEEE publishes more than 1,800 leading-edge conference proceedings every year, which are recognized by academia and industry worldwide as the most vital collection of consolidated published papers in electrical engineering, computer science, and related fields.
IEEE Transactions on Computers (TC), the flagship journal for the IEEE Computer Society, is a monthly publication with a wide distribution to researchers, developers, technical managers, and educators in the computer field. It publishes papers on research in areas of current interest to the readers, including but not limited to the following ...
Join an IEEE Society. Enhance your education and professional development. Join an IEEE Society and gain free access webinars, conference presentations, workshops, and more in your field. ... Select one or more search filters below to refine the resources displayed on this page. Category. open access papers 41; Publications 41; Media Type. PDF ...
Top 10 Published Articles of IEEE Access Over the past ten years, IEEE Access has published some of the most groundbreaking research in electrical and electronics engineering and computer science. In celebration of the 10 Year Publishing Anniversary, our Editors have selected the Top 10 articles published in IEEE Access over the last decade based on downloads, citations, and overall impact in ...
Cognitive load (CL), the mental effort required to process information, plays a pivotal role in user performance and experience in various domains, particularly within computer science (CS) and information systems (IS). As technology becomes more interactive and complex, understanding and measuring CL has become increasingly important for the design of adaptive and user-centered systems. This ...
IEEE publishes more than 1,700 leading-edge conference proceedings every year, which are recognized by academia and industry worldwide as the most vital collection of consolidated published papers in electrical engineering, computer science, and related fields.